Excerpt
When a trusted partner’s emails started landing in spam (or nowhere at all), I traced the path, set a top-priority allow rule, and used Defender’s Allow/Block list to force clean delivery—without exposing internal details.
Intro
Today’s note is for admins who wear the on-call hat. Messages from [partner-domain] weren’t reaching our users. Some were quarantined as spam; others never showed. I documented the exact, reversible steps I used to restore delivery while keeping our environment safe and auditable. All vendor names, mailboxes, IPs, and hostnames are redacted.
Notes from {Speaker}
- Symptom: Mail from [partner-domain] was flagged/filtered; end users reported “not delivered” or “went to Junk.”
- Tools used: Exchange Admin Center, Microsoft 365 Defender, Exchange Online PowerShell.
- Constraints: Multiple legacy transport rules; need a change that’s surgical, auditable, and easy to roll back.
- Guardrails: Prefer allowlisting at the domain + spoof layer (not blanket bypass for everything). Keep headers/SPF/DKIM intact for future tuning.
Perspective (direct quotes)
“No decision is a decision—so we’ll choose the safe, reversible one.”
“Top-priority SCL-1 with Stop processing beats noisy downstream rules.”
“If spoof intelligence is tripping, meet it where it lives: Tenant Allow/Block.”
Practice (today, not someday)
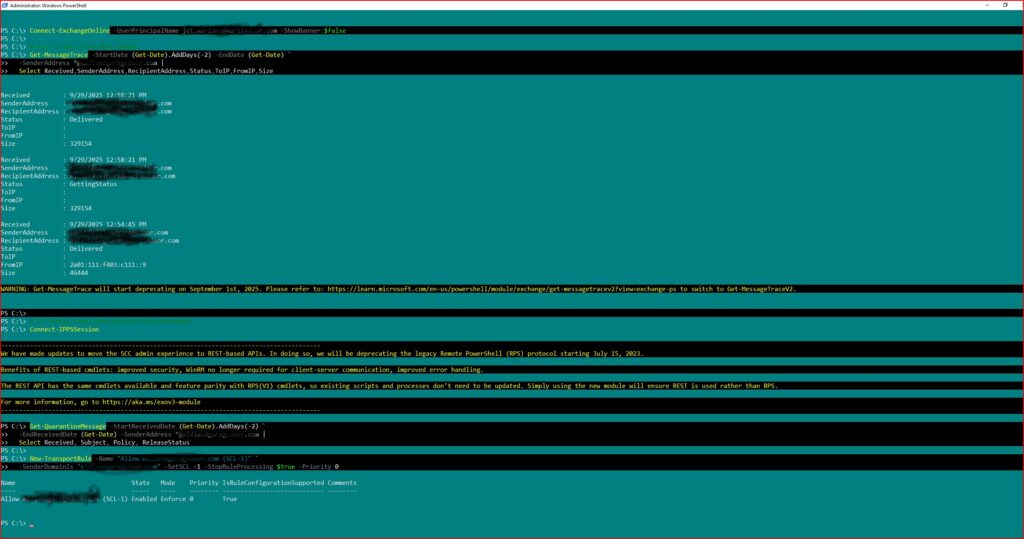
1) Triage — see what actually happened
Connect-ExchangeOnline -UserPrincipalName [me] -ShowBanner:$false
Get-MessageTrace -StartDate (Get-Date).AddDays(-2) -EndDate (Get-Date) `
-SenderAddress *@[partner-domain] |
Select Received,SenderAddress,RecipientAddress,Status
# If quarantined:
Connect-IPPSSession
Get-QuarantineMessage -StartReceivedDate (Get-Date).AddDays(-2) `
-EndReceivedDate (Get-Date) -SenderAddress *@[partner-domain]
2) Create a top-priority transport rule to force deliver
- Condition: Sender domain is [partner-domain]
- Action: Set SCL to -1
- Option: Stop processing more rules
- Priority: 0 (top)
PowerShell (redacted names):
New-TransportRule -Name "Allow [partner-domain] (SCL-1)" `
-SenderDomainIs "[partner-domain]" -SetSCL -1 -StopRuleProcessing $true -Priority 0
3) Add an org-wide Allow (Defender)
- Defender → Policies & rules → Tenant Allow/Block List
- Domains & addresses → Add → Allow → [partner-domain]
- If Message Trace shows Spoof/High Confidence Phish, also allow under Spoofing for the exact sending pair.
4) (Optional) Anti-spam policy allow list
- Anti-spam inbound policy → Allowed domains → add [partner-domain].
5) Verify
Get-TransportRule "Allow [partner-domain] (SCL-1)" |
fl Name,Priority,State,SenderDomainIs,SetSCL,StopRuleProcessing
# Send a new test; re-run Get-MessageTrace to confirm Status = Delivered
6) Longer-term hygiene (ask the sender)
- Ensure SPF passes (include correct outbound hosts).
- Turn on DKIM for their domain.
- Align DMARC policy gradually (none → quarantine → reject) once stable.
Final Reflection
Most “email is broken” moments aren’t outages—they’re safety systems doing their job a bit too eagerly. The win is balancing protection with precision so real mail flows and risky mail doesn’t.
Pocket I’m Keeping
Put the SCL-1 allow rule with Stop Processing at the top. It’s decisive, reversible, and neutralizes noisy legacy rules downstream.
What I Hear Now (direct quotes)
“Measure twice, move to Priority 0 once.”
“Don’t fight spoof intelligence—configure it.”
“Document the rollback the same minute you deploy the fix.”
- Microsoft 365 Defender — Tenant Allow/Block List (TABL)
- Exchange Online — Transport rules (mail flow rules)
- Message trace in the modern EAC
(references listed for context; links omitted for privacy—add your preferred docs when publishing)
© 2012–2025 Jet Mariano. All rights reserved.
For usage terms, please see the Legal Disclaimer.